ByBit Hack: What Happened and How It Changed Crypto Security
When the ByBit hack, a major security breach at one of the world’s largest crypto exchanges that led to significant asset losses happened, it wasn’t just another headline—it was a wake-up call for everyone holding crypto online. The attack didn’t target a small, unknown platform. ByBit was a top-tier exchange with multi-sig wallets, cold storage, and a reputation for strong security. Yet, attackers still got in. How? The answer isn’t magic. It’s human error, misconfigured systems, and the fact that even the best exchanges are only as strong as their weakest link.
The crypto exchange security, the set of practices and technologies used to protect user funds on trading platforms model has been built on trust, not proof. Exchanges promise safety, but they’re still centralized targets. The exchange hack, a deliberate attack on a crypto platform to steal digital assets on ByBit showed that even with advanced tools, internal access controls and third-party integrations can be exploited. This wasn’t a smart contract bug like in DeFi. It was a breach inside the exchange’s own infrastructure—likely through a compromised employee account or an unpatched API. The result? Millions lost, trust shaken, and users scrambling to move funds to self-custody.
After the ByBit hack, the industry didn’t just patch a hole. It started asking harder questions. Why do exchanges hold so much user crypto in hot wallets? Why aren’t withdrawal limits stricter? Why do so many platforms still rely on SMS for 2FA? The cryptocurrency theft, the unauthorized taking of digital assets through hacking, phishing, or social engineering that followed forced users to realize: if you don’t control the keys, you don’t own the crypto. That’s why more people started using hardware wallets, moving to non-custodial platforms, and learning how to verify withdrawal addresses manually.
What’s changed since then? More exchanges now use time-delayed withdrawals, require multi-person approvals for large transfers, and publish regular proof-of-reserves audits. But the real shift is in user behavior. People are no longer just clicking "Deposit" and forgetting about it. They’re asking: Where is my money stored? Who has access? Can I withdraw it anytime without asking permission? The blockchain security, the overall integrity and protection of blockchain networks and connected services from malicious activity isn’t just about the tech anymore—it’s about the habits of the people using it.
Below, you’ll find real case studies, breakdowns of how similar hacks unfolded, and clear guides on how to protect yourself—not just from exchange breaches, but from the tricks that follow them. These aren’t theory pieces. They’re lessons from people who lost money, got scammed, or narrowly avoided disaster. You don’t need to be a tech expert to stay safe. You just need to know what to look for.

ByBit Hack: How North Korea Stole $1.5 Billion in Crypto
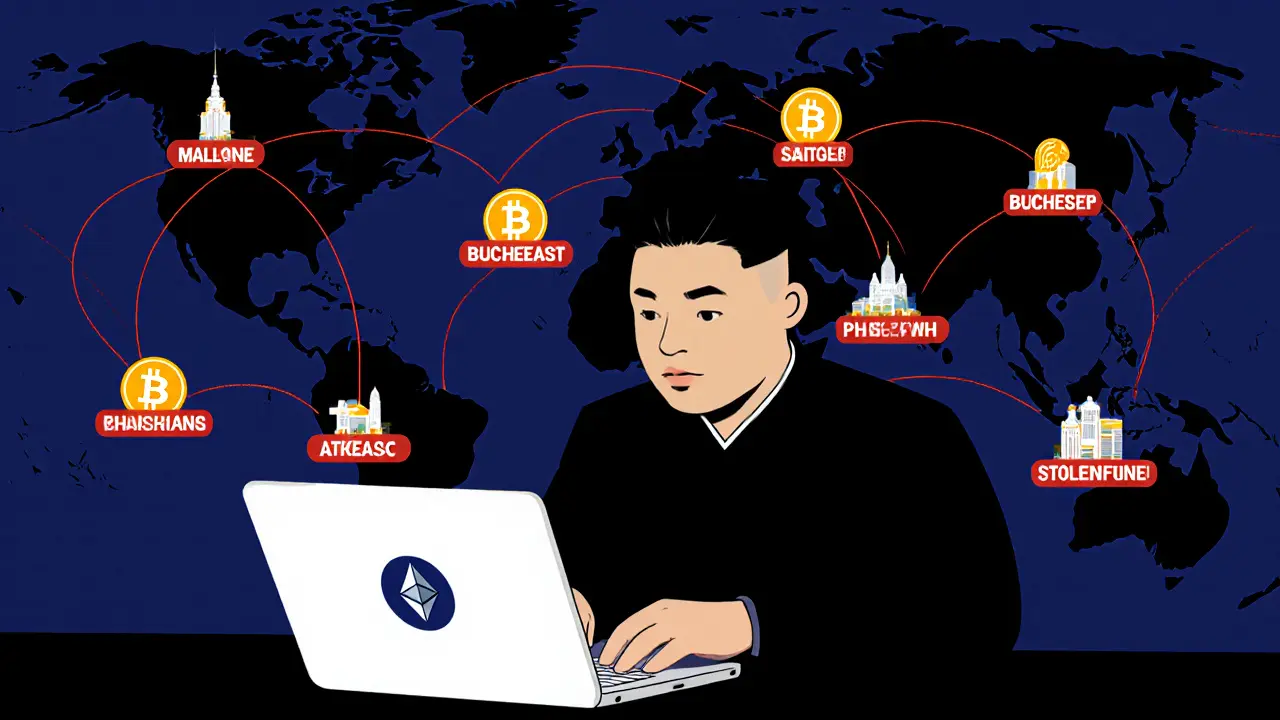
In February 2025, North Korea's TraderTraitor unit stole $1.5 billion from Bybit-the biggest crypto heist ever. This wasn't random hacking. It was a state-sponsored attack that exposed critical flaws in crypto security.
North Korea Crypto Ban and State-Sponsored Hacking Operations in 2025
North Korea stole over $2.17 billion in crypto in 2025, mostly through the ByBit hack. State-sponsored hackers use remote workers and Cambodia-based laundering networks to fund nuclear programs. Here's how it works - and why it's getting harder to stop.
© 2026. All rights reserved.